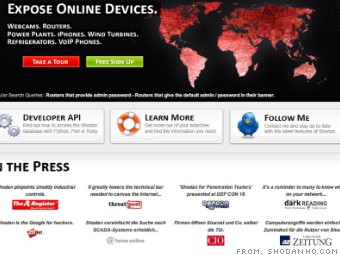
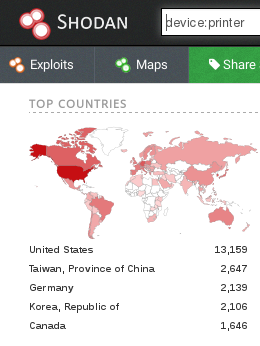
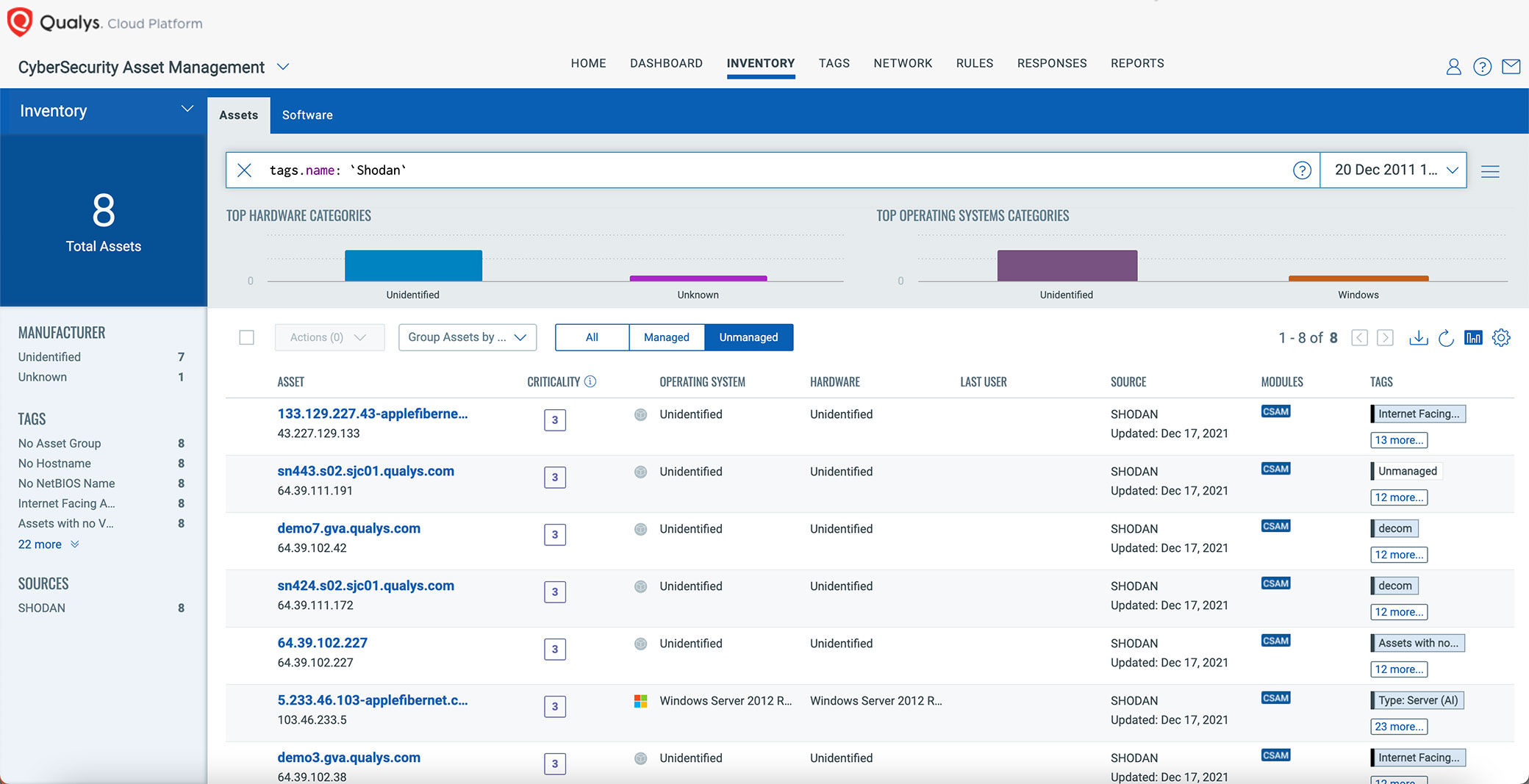
Cybersecurity Prism - What Is Shodan Exactly? You certainly know what Google is: it's a search engine that finds websites. However, it only scratches the surface of what we can find on

Insights from the PewDiePie Hack: Trends in Strengthening Public Sector Printer Security – Connected IT Blog
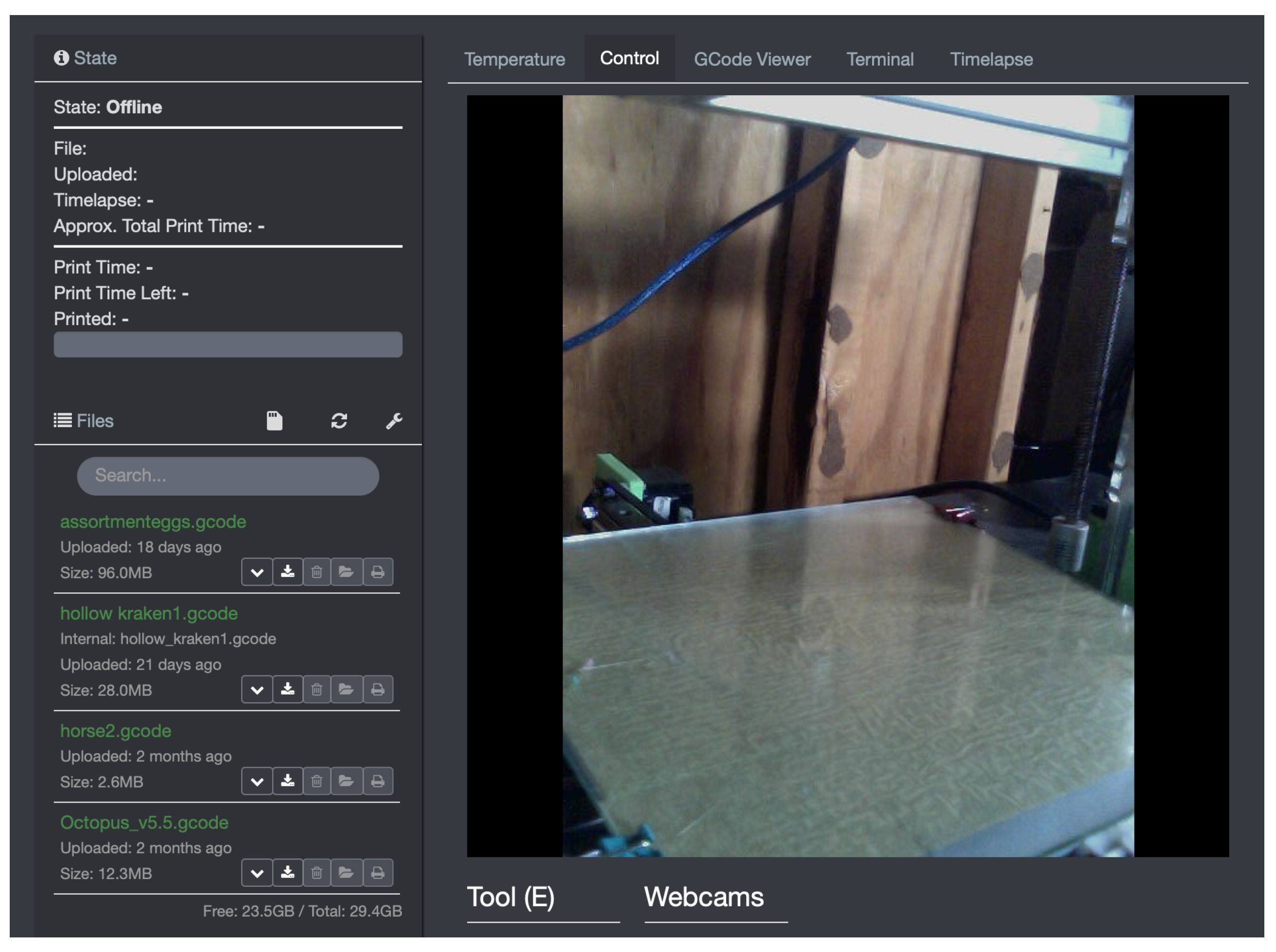
Applied Sciences | Free Full-Text | Use Case Based Blended Teaching of IIoT Cybersecurity in the Industry 4.0 Era
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases










![Complete Guide to… by John Matherly [Leanpub PDF/iPad/Kindle] Complete Guide to… by John Matherly [Leanpub PDF/iPad/Kindle]](https://d2sofvawe08yqg.cloudfront.net/shodan/s_hero2x?1620485817)